A TCP/IP network connection may be either blocked, dropped, open, or filtered. These actions are generally controlled by the IPtables firewall the system uses and is independent of any process or program that may be listening on a network port. Beyond the firewall, a program or process (a server or daemon) may be listening on a port or not listening. This can be checked using the netstat programs. Checking to see if a port is open, blocked, dropped, or filtered at the firewall is not simple.
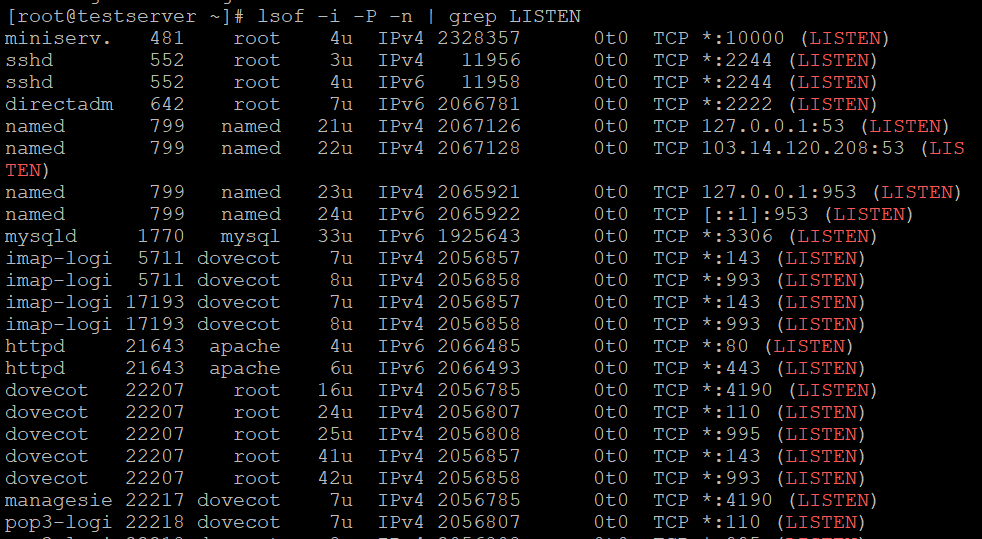
Using lsof to find open ports:
lsof -i:22 ## see a specific port such as 22 ##
lsof -i -P -n | grep LISTEN
You can run any one of the above commands
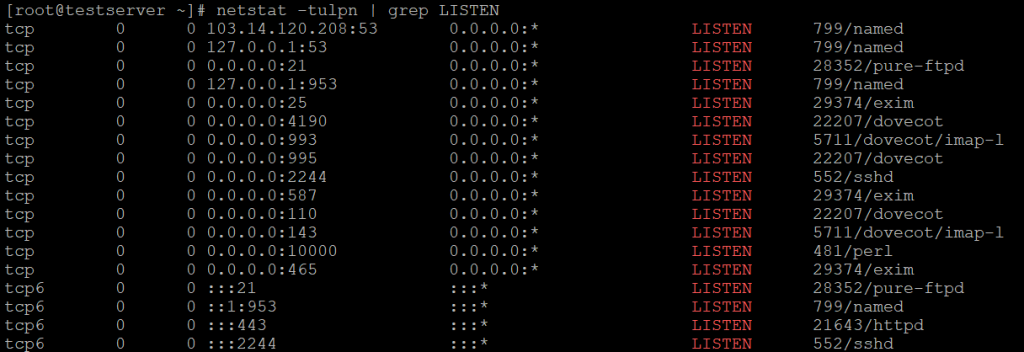
Using netstat to see the listening processes:
Run netstat command along with grep command to filter out port in LISTEN state:
netstat -tulpn | grep LISTEN
t – Show TCP
u – Show UDP
l – Show only listening processes (netstat can show both listening and all established connections, i.e. as a client too)
n – Do not resolve network IP address names or port numbers
p – Show the process name that is listening on the port
You can check port usage from Windows operating system using following command:
netstat -bano | more
netstat -bano | grep LISTENING
netstat -bano | findstr /R /C:”[LISTEING]”
We hope you’ve found this useful!